In the ever-evolving landscape of cryptocurrency, security stands as a paramount concern. The rise of digital assets has given rise to a corresponding increase in cyber threats, making it imperative for individuals and organizations ....
The realm of cybersecurity is a relentless battleground, with adversaries constantly evolving their tactics, techniques, and procedures (TTPs). To effectively combat these threats, cybersecurity consulting ..
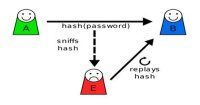
In the rapidly evolving landscape of cybersecurity, new threats continually emerge, challenging the resilience of cryptographic protocols. One such threat that has gained notoriety for its stealthy nature and ability to undermine ...
In an age where digital connectivity and technological advancement have become the cornerstones of modern life, the threat of cyberattacks looms larger than ever. No entity, whether a small enterprise or a corporate giant, ..
Ganesh Chaturthi, one of India's most vibrant and cherished festivals, brings people together in celebration of Lord Ganesha, the remover of obstacles and the god of wisdom and beginnings.On the 16th of September 2023, DigiALERT - ...
Onam, the vibrant and culturally rich festival of Kerala, holds a special place in the hearts of Malayalees around the world. It's a time when families come together to celebrate the harvest season with elaborate feasts, traditional dances, and colorful floral decorations....
In today's interconnected digital landscape, organizations rely heavily on computer networks to manage their resources and facilitate communication. One of the central components that governs access and permissions ...
In the dynamic realm of cybersecurity, constant vigilance is crucial to ensure the safety and integrity of web applications. HTML5, the latest iteration of the Hypertext Markup Language, has introduced groundbreaking ...
In our digital world, information is valuable, and bad guys are always trying to steal it. One way they do this is by using something called "Info Stealer Malware." This blog will explain what Info Stealer Malware is,..
In today's rapidly evolving digital landscape, cybersecurity stands as a paramount concern for organizations across the globe. Cyber threats continue to advance in sophistication and scope, targeting businesses of all sizes and industries....