In the fast-evolving digital landscape, nations are grappling with the relentless onslaught of cyber threats that transcend borders and institutions. The recent revelation of cyber attacks targeting the Assembly ...
Cracking Down on Cyber Threats: Malaysian Authorities Dismantle BulletProofLink Phishing-as-a-Service Operation
KalirajIn a pivotal moment in the ongoing battle against cybercrime, Malaysian law enforcement authorities, in conjunction with the Australian Federal Police (AFP) and the U.S. Federal Bureau of Investigation (FBI),..
Navigating the Crypto Storm: Understanding and Countering the Surge in Phishing Attacks and Wallet-Draining Techniques
KalirajIn the dynamic realm of cryptocurrency, innovation is often accompanied by challenges, and currently, a formidable one is emerging – a surge in sophisticated phishing attacks targeting cryptocurrency wallets...
In the intricate world of cybersecurity, where adversaries are perpetually refining their techniques, the discovery of Operation Triangulation by Russian cybersecurity firm Kaspersky stands out as a watershed moment....
In an era characterized by rapid technological advancement, the realm of cybersecurity faces unprecedented challenges. As organizations embrace digital transformation, the sheer volume of data generated becomes both a boon and a bane...
As we immerse ourselves in the digital era, safeguarding our online assets has become an imperative task. With cyber threats evolving continuously, it is essential to fortify our defenses. This comprehensive guide aims ...
In an age of rapid technological evolution, the advent of 5G technology promises unparalleled connectivity and speed. While its potential benefits are vast, a critical examination of the associated security implications is imperative.....
In the intricate tapestry of cybersecurity, encryption stands as a formidable barrier against prying eyes and potential threats. Among the myriad encryption tools available, Pretty Good Privacy (PGP) has emerged ....
Living in an age dominated by digital interactions, the imperative for robust cybersecurity measures has never been more pronounced. Amidst the multitude of tools available for online protection, the Virtual Private Network (VPN)...
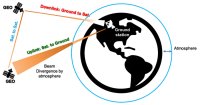
In the expansive realm of cybersecurity, where threats constantly evolve, the role of satellite bandwidth often remains overlooked. The global reliance on satellites for communication and data transmission ...