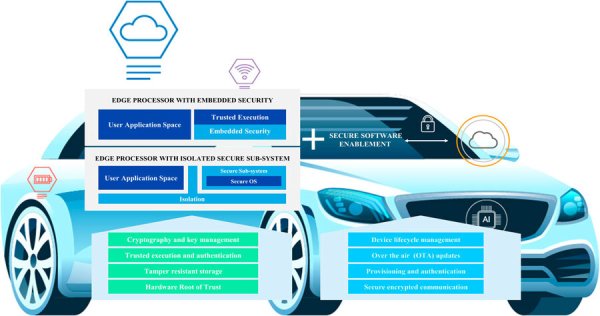
In the ever-evolving sphere of technology, Over-the-Air (OTA) updates have emerged as a linchpin for the maintenance and advancement of connected devices. From the ubiquitous smartphone and smart TV to the complex systems in automobiles and the myriad of devices in the Internet of Things (IoT) ecosystem, the advent of OTA updates has streamlined the process of delivering software enhancements directly to devices over the internet. However, the increasing prevalence of OTA updates necessitates a parallel emphasis on robust cybersecurity measures to thwart potential threats. This blog delves into the multifaceted realm of OTA updates, unraveling their significance, and shedding light on the critical cybersecurity considerations integral to their effective implementation and management.
Understanding Over-the-Air (OTA) Updates
Definition and Imperative
Over-the-Air (OTA) updates represent the wireless delivery mechanism employed to disseminate new software or firmware to devices sans the need for physical connections. This method has garnered widespread acclaim due to its efficiency in deploying updates, fortifying security, and rectifying vulnerabilities without causing disruptions for end-users.
Expanding Horizons of OTA Updates
The purview of OTA updates spans across diverse industries encompassing automotive, healthcare, consumer electronics, and industrial IoT. As the tapestry of connected devices becomes more intricate, the capability to remotely update software emerges as paramount for maintaining security and adapting to the relentless evolution of cyber threats.
Benefits of OTA Updates
Prompt Mitigation of Vulnerabilities
Chief among the advantages of OTA updates is the expeditious response to security vulnerabilities. Manufacturers can swiftly dispatch patches and updates in real-time, effectively reducing the window of opportunity for potential cyber threats to exploit vulnerabilities.
Feature Augmentation and Performance Optimization
OTA updates not only serve the purpose of enhancing security but also afford manufacturers the flexibility to introduce novel features and optimize device performance. This agility ensures that devices remain relevant and resilient in the face of an ever-changing technological landscape.
Cybersecurity Challenges in OTA Updates
Data Integrity and Authenticity
Ensuring the integrity and authenticity of updates stands out as a pivotal challenge. Cyber adversaries may seek to compromise the update process, delivering nefarious software that could result in data breaches or unauthorized access to devices.
Secure Communication Channels
The establishment of secure communication channels between update servers and devices is paramount. Encryption protocols must be diligently implemented to shield the confidentiality of transmitted data, precluding eavesdropping or man-in-the-middle attacks.
Device Authentication and Authorization
OTA updates must only be accepted from authenticated and authorized sources. The implementation of robust authentication mechanisms guarantees that devices solely receive updates from legitimate sources, thereby mitigating the risk of accepting malicious updates.
Best Practices for Secure OTA Updates
Code Signing
The adoption of code signing serves as a linchpin in ensuring that updates emanate from a trusted source. Digital signatures play a pivotal role in validating the authenticity of the update, providing an additional layer of security against unauthorized modifications.
Secure Boot Process
Integrating a secure boot process assumes critical importance in the context of OTA updates. This mechanism ensures that only authenticated and unmodified code is executed during the device's startup, thus precluding the execution of malicious code that could compromise the security of the device.
Continuous Monitoring and Auditing
Regular monitoring and auditing of the OTA update process are indispensable. This proactive approach aids in the identification of anomalies or suspicious activities, enabling swift responses to potential security threats and minimizing the impact on device security.
Examples and Evidence:
1. Tesla's Remote Patching:
- Example In 2020, Tesla demonstrated the power of OTA updates by remotely patching a vulnerability that could have allowed hackers to take control of a vehicle's central touchscreen.
- Evidence: This swift response illustrates the practical application of remote patching in the automotive sector, showcasing the importance of OTA updates in addressing security vulnerabilities in connected vehicles.
2. Mobile Operating Systems:
- Example: iOS and Android regularly release OTA updates to address security vulnerabilities and improve device performance.
- Evidence: Frequent security patches from Apple and Google through OTA updates highlight the crucial role of these updates in maintaining the security of widely used mobile operating systems.
3. Automotive Cybersecurity Best Practices (WP.29):
- Example: WP.29, established by the United Nations Economic Commission for Europe, includes guidelines for automotive cybersecurity, emphasizing the importance of secure OTA updates.
- Evidence: This global initiative underscores the industry's recognition of OTA updates as a crucial element in safeguarding connected vehicles against cyber threats.
4. Medical Device Security:
- Example: The healthcare industry relies on connected medical devices that receive updates to address security vulnerabilities and ensure patient safety.
- Evidence: Regulatory bodies like the U.S. FDA emphasize the importance of timely security updates for medical devices. Instances of vulnerabilities in medical devices have prompted manufacturers to implement OTA updates to protect patient well-being.
5. Equifax Data Breach:
- Example: The Equifax data breach in 2017 exposed sensitive personal information due to unpatched software vulnerabilities.
- Evidence: This incident highlights the consequences of failing to apply security updates promptly. Timely OTA updates could have mitigated the impact of the breach.
6. NotPetya Ransomware Attack:
- Example: The NotPetya ransomware attack in 2017 exploited unpatched systems, causing widespread disruptions and financial losses.
- Evidence: Organizations affected by NotPetya suffered due to the exploitation of unpatched vulnerabilities, emphasizing the critical role of timely updates, including OTA updates.
7. Ponemon Institute's Cost of Cyber-Crime Study:
- Example: The Ponemon Institute conducts studies on the financial impact of cybercrime, including the costs associated with unpatched vulnerabilities.
- Evidence: Reports from Ponemon consistently highlight the financial losses incurred by organizations due to cyber incidents. Timely application of security patches, facilitated by OTA updates, emerges as a cost-effective strategy.
8. National Vulnerability Database (NVD):
- Example: The NVD, maintained by NIST, catalogues and analyzes vulnerabilities in software and hardware.
- Evidence: Regular updates from NVD provide evidence on the prevalence of vulnerabilities and the importance of prompt updates. The data underscores the critical role of OTA updates in mitigating risks.
9. 5G and IoT Security:
- Example: The advent of 5G networks and the proliferation of IoT devices introduce new cybersecurity challenges, highlighting the need for secure OTA updates.
- Evidence: With the increasing interconnectivity facilitated by 5G and the surge in IoT devices, the incorporation of secure OTA update mechanisms becomes crucial to addressing vulnerabilities and ensuring resilience.
10. Zero-Day Exploits:
- Example: Zero-day exploits, targeting undisclosed vulnerabilities, pose significant threats to software and systems.
- Evidence: OTA updates serve as a proactive defense against zero-day exploits by enabling rapid deployment of patches once vulnerabilities are discovered. The ability to swiftly address unknown threats through OTA updates is crucial in mitigating evolving cyber risks.
Conclusion
In the dynamic realm of cybersecurity, the exploration of Over-the-Air (OTA) updates emerges as a cornerstone in fortifying digital ecosystems against evolving threats. As we navigate the intricate web of interconnected devices and systems, digiALERT's commitment to a comprehensive approach to OTA updates becomes increasingly evident.
The real-world examples vividly showcase the tangible impact of OTA updates. From Tesla's swift response to potential vehicle vulnerabilities to the regular security patches rolled out by major mobile operating systems like iOS and Android, the efficacy of OTA updates in addressing security concerns is unequivocal.
Industry standards and regulations, exemplified by the Automotive Cybersecurity Best Practices (WP.29) and the imperative placed on medical device security, underscore the global recognition of OTA updates as a linchpin in securing critical sectors. In the automotive domain, WP.29 lays down guidelines that emphasize the significance of secure OTA updates in protecting connected vehicles from cyber threats, aligning seamlessly with digiALERT's commitment to excellence.
Lessons learned from cybersecurity incidents, such as the Equifax data breach and the NotPetya ransomware attack, underline the consequences of neglecting timely updates. The correlation between unpatched vulnerabilities and successful cyberattacks emphasizes the urgency of proactive measures, precisely the ethos encapsulated by digiALERT's approach to OTA updates.
Research and studies, exemplified by the Ponemon Institute's Cost of Cyber-Crime Study and the National Vulnerability Database (NVD), provide a data-driven perspective on the financial impact of cyber incidents and the prevalence of vulnerabilities. These insights validate digiALERT's holistic strategy, positioning OTA updates as not just a reactive measure but a proactive and cost-effective defense against cyber threats.
Looking ahead, as 5G and the Internet of Things (IoT) redefine connectivity landscapes, digiALERT's commitment to secure OTA updates remains pivotal. The company's acknowledgment of the interplay between emerging technologies and the need for resilient update mechanisms positions them at the forefront of cybersecurity innovation.
In the face of zero-day exploits and unknown threats, the conclusion is clear – OTA updates represent a powerful tool in digiALERT's arsenal. The ability to swiftly deploy patches and updates serves as a proactive defense mechanism, aligning with the company's commitment to staying one step ahead of cyber adversaries.
As we conclude this exploration, it's evident that digiALERT's comprehensive approach to OTA updates is not merely a strategy; it's a commitment to cybersecurity excellence. In the ever-evolving digital landscape, where threats loom large and vulnerabilities abound, the role of OTA updates in fortifying our digital defenses is undeniable. DigiALERT's journey through this exploration exemplifies not just a response to cybersecurity challenges but a proactive stance, ensuring that the digital highway remains secure, resilient, and ready to face the challenges of tomorrow.