Vulnerability Assessment and Pentesting (41)
In the ever-expanding realm of cybersecurity, few threats loom as ominously as ransomware. Recent developments in the tactics and targets of ransomware groups highlight the dynamic and relentless nature of these malicious actors.....
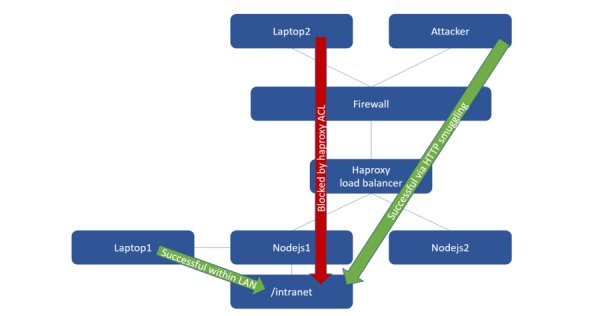
In the ever-evolving landscape of cybersecurity, new threats and attack vectors continuously emerge, challenging the resilience of organizations and individuals alike. One such threat that has recently surfaced is the utilization...
In a digital age fraught with cyber threats, the recent revelation of a significant breach at Microsoft has sent shockwaves through the cybersecurity community. The breach, orchestrated by the Kremlin-backed threat group Midnight Blizzard,...
The digital world is a dynamic ecosystem, constantly evolving with new technologies and innovations. However, this evolution also brings forth new challenges, particularly in the realm of cybersecurity. In recent times,...
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is not just a best practice; it's a necessity. Recently, a significant vulnerability in Microsoft Outlook came to light, leaving users susceptible to potential exploits....
In the dynamic realm of cybersecurity, threats continue to evolve, with each new adversary presenting unique challenges for developers and organizations. A recent addition to this landscape is MavenGate,..
In the dynamic realm of cybersecurity, staying ahead of sophisticated threats is imperative. A recent breakthrough has emerged in the form of iShutdown, a lightweight yet robust method designed to expose spyware on Apple iOS devices...
In the complex and ever-shifting landscape of cybersecurity, threats to digital assets continue to evolve, with state-sponsored actors taking center stage. One such disconcerting development is the increasing prowess of North Korea ....
The intricate landscape of cybersecurity is witnessing a renewed assault as Dutch IT and telecom companies find themselves ensnared in the web of a sophisticated cyber espionage campaign....
Blockchain and Cybersecurity: Analyzing the Transformative Impact on Application and System Security
In the contemporary digital landscape, characterized by relentless technological advancement, the imperative of robust cybersecurity measures cannot be overstated. As the threat landscape becomes increasingly sophisticated,..
More...
In the ever-expanding realm of cybersecurity, the persistent menace of phishing attacks stands out as a formidable threat. These insidious tactics prey upon the vulnerabilities of individuals and organizations alike,..
In today's rapidly evolving landscape of cybersecurity, biometric authentication has emerged as a prominent and cutting-edge security technology. Biometrics, the science of measuring and analyzing unique physical and behavioral..
In the dynamic realm of cybersecurity, new threats continually emerge, often adapting to the latest technologies. GraphQL, a versatile query language for APIs, has gained widespread popularity in recent years due to its flexibility and efficiency...
In the ever-evolving landscape of cybersecurity, certain adversaries have gained notoriety for their stealthy tactics and relentless attacks. One such formidable adversary is "Mimikatz." This blog post embarks on an extensive journey..