Security Assessment (36)
In the ever-expanding digital realm, cybersecurity remains a paramount concern. Recent discoveries have unveiled two significant threats: the extensive DNS probing campaign orchestrated by the enigmatic Chinese actor known as SecShow and the rise of Rebirth,...
In today's interconnected digital world, security vulnerabilities in widely-used software libraries can have far-reaching consequences. Recently, researchers uncovered significant flaws in two such libraries: the llama_cpp_python package, ...
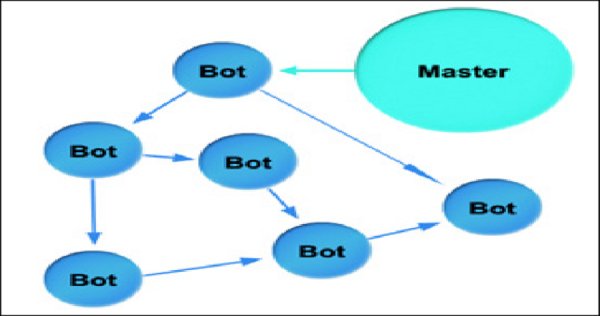
The cybersecurity landscape continues to evolve rapidly, with threat actors employing increasingly sophisticated methods to compromise systems and steal sensitive information. Among the most concerning developments is the activity...
The digital age has brought about tremendous convenience and connectivity, with smartphones and mobile apps becoming an integral part of our daily lives. However, alongside these advancements come....
The digital age has ushered in an era of unprecedented connectivity, with Internet of Things (IoT) devices becoming ubiquitous in our daily lives. From smart thermostats to voice-activated assistants, these devices offer convenience and efficiency....
The digital landscape of today's world has revolutionized the way we conduct business, with e-commerce platforms serving as the cornerstone of online retail. However, along with the convenience and accessibility....
In today's interconnected digital world, cybersecurity threats continue to evolve at an alarming rate. As organizations strive to protect their assets and sensitive information, a new malware strain has emerged,...
Cybersecurity threats continue to evolve at a rapid pace, posing significant challenges to organizations worldwide. In recent times, the emergence of China-linked hacker groups exploiting security flaws in Ivanti appliances has garnered..
The realm of cybersecurity is constantly challenged by the emergence of new threat actors, each with their own techniques and motivations. Among these, CoralRaider stands out as a significant menace, operating with sophistication and precision to target victims across Asia and Southeast Asia....
In an age where smartphones are the hub of our digital lives, the integrity of mobile security is paramount. Recent revelations have brought to light a new chapter in the saga of cyber threats targeting Android devices...
More...
In the intricate world of cybersecurity, the software supply chain has emerged as a prime target for malicious actors seeking to infiltrate systems and wreak havoc. The recent revelation of a backdoor in XZ Utils,...
The hospitality industry has undergone a digital revolution in recent years, with electronic RFID locks becoming a ubiquitous feature in hotel rooms across the globe. These locks offer convenience and security to both guests and hotel management....
In the realm of cybersecurity, the software supply chain stands as a critical yet vulnerable component. Recent revelations surrounding the suspicious NuGet package, SqzrFramework480, serve as a stark reminder ...
In today's interconnected digital world, cybersecurity remains a critical concern for individuals and organizations alike. As technology advances, so too do the tactics employed by cybercriminals seeking to exploit vulnerabilities for financial gain or malicious intent....