In an era where technology permeates every facet of our lives, the Global Positioning System (GPS) has become an indispensable tool, seamlessly integrated into navigation systems, transportation, and various industries. However, as our reliance on GPS grows, so does the potential for cyber threats, with GPS spoofing emerging as a particularly insidious danger. This blog aims to provide an in-depth exploration of GPS spoofing, unraveling its complexities, exploring potential risks, and delving into countermeasures to fortify our systems against this evolving threat.
What is GPS Spoofing?
Defining GPS Spoofing
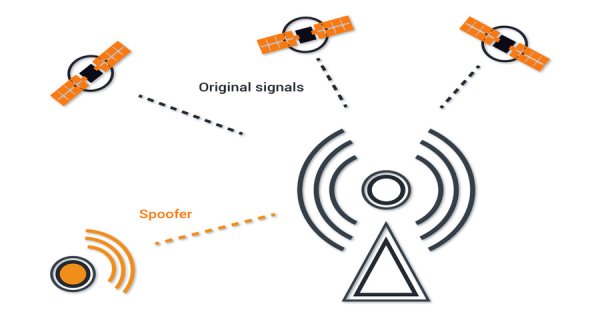
At its core, GPS spoofing involves the manipulation of GPS signals to deceive receivers, offering false information about a user's location, time, or velocity. Unlike GPS jamming, which disrupts signals, GPS spoofing is a more nefarious practice that actively transmits counterfeit signals to mislead GPS receivers.
How GPS Works
Before dissecting the intricacies of GPS spoofing, it's imperative to comprehend the fundamental workings of the Global Positioning System. GPS relies on a constellation of satellites orbiting Earth, each emitting signals containing precise timing information. GPS receivers on the ground use these signals to triangulate their position accurately. Spoofing interferes with this process by broadcasting deceptive signals, leading receivers to calculate inaccurate positions.
Potential Risks and Consequences
Navigation Errors
The immediate and perhaps most evident consequence of GPS spoofing is navigation errors. Vehicles, ships, and aircraft that rely on GPS for navigation may find themselves directed off-course, potentially resulting in accidents or unintended deviations from planned routes.
Critical Infrastructure Vulnerabilities
Beyond the realm of navigation, numerous industries, including finance, telecommunications, and energy, depend on GPS for synchronization and timing. Spoofing attacks on critical infrastructure can lead to disruptions, financial losses, and compromise national security by disrupting communication networks or energy grids.
Cyber Espionage
GPS spoofing serves as a potent tool for cyber espionage. By manipulating location data, malicious actors can deceive individuals or organizations, gaining unauthorized access or surreptitiously monitoring sensitive activities. This adds a layer of complexity to traditional cyber threats, as physical locations become manipulated components in the digital realm.
Notable GPS Spoofing Incidents
- Iranian Capture of the U.S. Drone
One of the most widely reported instances of GPS spoofing occurred in 2011 when Iran claimed to have captured a U.S. RQ-170 Sentinel drone. According to reports, Iranian forces allegedly used GPS spoofing to deceive the drone's navigation system, redirecting it to land within Iranian territory. This incident highlighted the real-world implications of GPS spoofing in geopolitical conflicts.
- Shanghai Superyacht Race
In a more controlled environment, researchers demonstrated the potential dangers of GPS spoofing during a superyacht race in Shanghai in 2013. The team successfully executed a GPS spoofing attack, causing the participating yachts to veer off course without the knowledge of the crew. This experiment underscored the vulnerability of GPS systems, even in scenarios where one might assume a high level of security.
Mitigating GPS Spoofing
Signal Authentication
One of the primary strategies for mitigating GPS spoofing involves implementing signal authentication mechanisms. By introducing cryptographic techniques into the GPS signal transmission process, receivers can verify the authenticity of incoming signals. This additional layer of security helps prevent the acceptance of spoofed signals, enhancing the overall resilience of GPS systems.
Advanced Anti-Spoofing Technologies
The ongoing evolution of technology presents opportunities to develop and deploy advanced anti-spoofing technologies. Multi-constellation receivers, for example, can leverage signals from multiple satellite constellations, making it more challenging for spoofers to manipulate signals consistently. Additionally, adaptive signal processing techniques can be employed to discern genuine signals from fraudulent ones, further bolstering the defenses against GPS spoofing.
Legislation and Regulation
Beyond technological solutions, enacting legislation and regulations is crucial to combating GPS spoofing effectively. Governments and international bodies must collaborate to establish comprehensive legal frameworks that deter and penalize GPS spoofing activities. This not only serves as a deterrent but also provides a basis for prosecuting offenders, creating a robust legal deterrent against malicious actors.
Examples and Evidence:
- Iranian Capture of the U.S. Drone (2011)
Example:
One of the most prominent examples of GPS spoofing in recent history involves the capture of a U.S. RQ-170 Sentinel drone by Iran in 2011.
Evidence:
- Official Claims: Iran officially claimed responsibility for capturing the drone and asserted that they had used GPS spoofing to manipulate the drone's navigation system, guiding it to land within Iranian territory.
- Confirmation by U.S.: While the U.S. initially denied Iran's claims, later statements acknowledged the loss of the drone but did not provide details about the specific cause. This incident highlighted the susceptibility of military-grade GPS systems to spoofing attacks.
- Shanghai Superyacht Race (2013)
Example:
In 2013, researchers conducted a GPS spoofing experiment during a superyacht race in Shanghai.
Evidence:
- Yacht Deviations: During the race, the researchers successfully executed a GPS spoofing attack, causing participating yachts to deviate from their intended course. The unsuspecting crews were unaware of the manipulated navigation data.
- Demonstration Video: The research team documented their experiment, providing a visual representation of how GPS spoofing could be exploited in a controlled environment. This tangible demonstration underscored the potential risks associated with GPS spoofing.
- Russian GNSS Spoofing (ongoing)
Example:
Russia has been implicated in multiple instances of GPS spoofing, particularly in the vicinity of sensitive locations.
Evidence:
- Reports by Aviation Authorities: Pilots and aviation authorities have reported incidents of GPS signal anomalies in regions near Russian military installations. These anomalies have led to navigation discrepancies for aircraft in those areas.
- Public Warnings: Various governments, including the United States, have issued public warnings to pilots and maritime operators about the potential for GPS signal disruptions in certain regions, citing the likelihood of Russian interference.
- GPS Spoofing in Cybersecurity Research
Example:
Several cybersecurity researchers have conducted experiments to demonstrate the vulnerabilities of GPS systems.
Evidence:
- University Research Projects: Academic institutions and cybersecurity research teams have published findings showcasing successful GPS spoofing attacks on consumer-grade GPS devices. These experiments often involve using software-defined radios to generate counterfeit GPS signals.
- Conference Presentations: Researchers frequently present their findings at cybersecurity conferences, detailing the methodologies and tools employed in their GPS spoofing experiments. These presentations contribute to the collective understanding of the vulnerabilities in GPS technology.
- Maritime Navigation Incidents
Example:
Incidents of GPS spoofing affecting maritime navigation have been reported in various regions.
Evidence:
- Navigation System Anomalies: Ships relying on GPS for navigation have reported sudden and inexplicable shifts in their perceived locations. These anomalies have been linked to GPS spoofing activities, potentially carried out for purposes ranging from territorial disputes to illegal activities.
- Official Investigations: Maritime authorities in affected regions have launched investigations into instances of GPS spoofing, seeking to understand the extent of the problem and identify responsible parties.
Conclusion
In the intricate landscape of digital connectivity, our exploration of "Understanding GPS Spoofing" has unveiled the lurking threats that compromise the reliability of Global Positioning Systems. As we navigate the vast expanses of cyberspace, the specter of GPS spoofing emerges as a formidable adversary, capable of inducing navigation errors, endangering critical infrastructure, and fostering cyber espionage.
In the realm of digital security, our commitment to fortifying our defenses against GPS spoofing takes center stage. As the architects of digiALERT, our responsibility extends beyond mere understanding; it compels us to action. Leveraging cutting-edge technologies and innovative strategies, we stand at the forefront of safeguarding our digital frontiers.
Through the implementation of signal authentication mechanisms, we erect formidable barriers against deceptive signals, ensuring the integrity of our GPS infrastructure. Advanced anti-spoofing technologies, such as multi-constellation receivers and adaptive signal processing, serve as the vanguard in our mission to outsmart potential adversaries.
Yet, in our arsenal against GPS spoofing, legislation and regulation stand as pillars of resilience. Collaborating with governments and international bodies, digiALERT advocates for comprehensive legal frameworks that not only deter potential wrongdoers but also empower us to prosecute those who seek to compromise the very fabric of our digital society.
As we draw this comprehensive overview to a close, it becomes abundantly clear that the future of digital security lies in our hands. Vigilance, innovation, and collaboration form the bedrock of our strategy against GPS spoofing. Together, with digiALERT leading the charge, we navigate towards a future where the integrity of our GPS systems remains unassailable, ensuring that our digital journey is secure, reliable, and steadfast in the face of evolving cyber threats.